"TLS-Set-Server-Trusted-Store" Options Dialog Page
In the previous version, built-in TLS Client was given ability to supply certificate to authenticate itself with TLS Server. In this new version, I have revamped the code in TLS Server that is responsible for checking certificate presented by TLS Client.

"TLS-Set-Server-Trusted-Store" Options Dialog Page
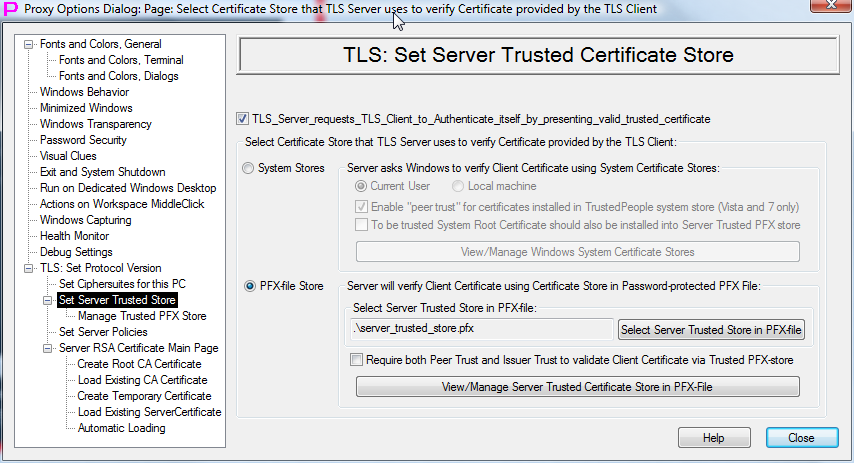
System certificate stores and associated with them Windows Certificate chain validation functions allow to maintain trust configuration at the user level and at the computer level. There are two types of trust for the system certificate store checks. "Issuer trust" (trust chain is starting from trusted root CAs in the system "Root" store) and "peer trust" (certificates that are present in the "TrustedPeople" System Certificate Store are trusted explicitly). By default, they are both enabled. "Peer trust" can be disabled by the checkmark "Enable ""peer trust"" for certificates installed in TrustedPeople system store (Vista and 7 only)". "Issuer trust" can be controlled or disabled by using PFX store to restrict system root store to only small subset of trusted root CA certs (check mark "To be trusted System Root Certificate should also be installed into Server Trusted PFX store"). In the previous version, "Enable ""peer trust"" for certificates installed in TrustedPeople system store (Vista and 7 only)" checkmark (on the Page "TLS Server Trusted Store" of the Options Dialog) when unselected was giving error message to server's terminal screen when peer trust was used, but TLS client that was passing "not enabled" peer trust (but was not passing issuer trust) was not disconnected automatically by TLS Server. In this new version, when peer trust is not enabled by checkmark, the TLS client that would be authenticated by peer trust (but not by issuer trust) is disconnected automatically by the TLS Server.
Trusted PFX certificate store of Proxy32 and associated with it Proxy32 internal Client Certificate validation functions allow to maintain trust configuration at the application level without need to modify user level and computer level trust configuration. In this new version, the code that validates TLS Client certificate via PFX-store is completely redesigned. To validate Client cert, either it should be present in PFX store (PEER TRUST) or its direct issuer (signer) should be present in the PFX store (ISSUER TRUST) or both should be present in PFX store (if checkmark "Require both Peer Trust and Issuer Trust to validate Client Certificate via Trusted PFX-store" is selected on the Page "TLS Server Trusted Store" of the Options Dialog). Client cert should be also with correct enhanced key usage (if it has such extension) and both client cert and issuer cert should not have expired. Bypass of certificate checks can be configured with the fine granularity via "Set TLS Server Policies" page in Options Dialog.
| step # | Description |
| 0. | If all cert checks are ignored, go to SUCCESS |
| 1. | Check time validity of the client Certificate |
| 2. | If time is invalid and no bypass of time check is enabled, then go to FAILURE |
| 3. | Check the Extended key usage extension of the Client Certificate |
| 4. | If Extended key usage is invalid (EKU Extension is present and does not contain Client AUTH in it) and no bypass of usage check is enabled, then go to FAILURE |
| 5. | Check if the Client Certificate is pre-installed in PFX store |
| 6. | If pre-installed (PEER TRUST is valid) and no "BOTH PEER TRUST and ISSUER TRUST are required", then go to SUCCESS |
| 7. | Look for the next issuer (signer) of the client certificate in the PFX store |
| 8. | if no next issuer found, or Client Cert is self-signed, go to FAILURE |
| 9. | Check signature of the issuer on the Client Cert and time validity of the issuer Cert |
| 10. | if signature of the issuer is bad and no bypass is enabled, go to step 7 to look for the next issuer |
| 11. | if time validity of the issuer is bad and no bypass is enabled, go to step 7 to look for the next issuer |
| 12. | ISSUER TRUST is valid. If no "BOTH PEER TRUST and ISSUER TRUST are required", then go to SUCCESS |
| 13. | if "BOTH PEER TRUST and ISSUER TRUST are required" and the Client Certificate is pre-installed in PFX store (result of step 5), then go to SUCCESS |
| 14. | FAILURE/EXIT |
| 15. | SUCCESS/EXIT |
Note: Bypass of various certificate checks can be configured with the fine granularity via "Set TLS Server Policies" page in Options Dialog.
Note: When check mark "To be trusted System Root Certificate should also be installed into Server Trusted PFX store" is selected in the Options Dialog page "TLS: Set Server Trusted Certificate Store", Proxy32 Trusted PFX store should contain only CA certificates (no end certificates) or Windows Certificate chain validation functions will give an error.